AWS IAM is a service that does authentication and authorization for AWS resource access.
IAM is a web service for securely controlling access to AWS resources. IAM gives control over who can access your AWS services and resources based on some predefined permissions.
Few important concepts in AWS IAM play crucial role in authentication and authorization
IAM Users
IAM Users is an entity created in AWS to provide a way o interact with AWS resources. A user in AWS consists of a name and credentials. It is not similar to AWS IAM root user. IAM users are provided specific access to AWS resources using IAM policies.
IAM Root Users
This is created by default when you create AWS account.A root user has full access to all the resources and assets in the AWS account.
Policies in AWS
AWS IAM policies regulate access to AWS resources to help ensure that only authorized users have access to specific resources. Root user provide access to specific resources to IAM Users using Policies.
User Groups in AWS
IAM groups are a collection of IAM users. User groups let you specify the permissions for multiple users which can make it easier to manage permissions of those users. Ex. We have group of developer that require some access to EC2 permissions . Then we can keep them in a group and give them permissions all together. Any new User added to this group will have these permissions. To remove permission of some users we just need to remove them from the group.
IAM Roles in AWS
IAM roles is similar to IAM users. It is an AWS identity with a permission policy of what it can do and what can not. It is not uniquely associated with one person but the role can be intended to anyone. Role doesn't have long term credentials. Roles have temporary security credentials for role session
To summarize IAM users help in authentication and Policies help in authorization for AWS resources/services.
Practical Steps
Let's learn step by step how to create IAM Users, Group and assign policies.
First we need to create an AWS account as root user. Link
We need to log in to AWS console. Navigate to IAM through search bar.
Click on Users -> Add users. Enter User name as needed. Select the tick box and select "I want to create an IAM user" and select the autogenerated password and create new password next time you login.
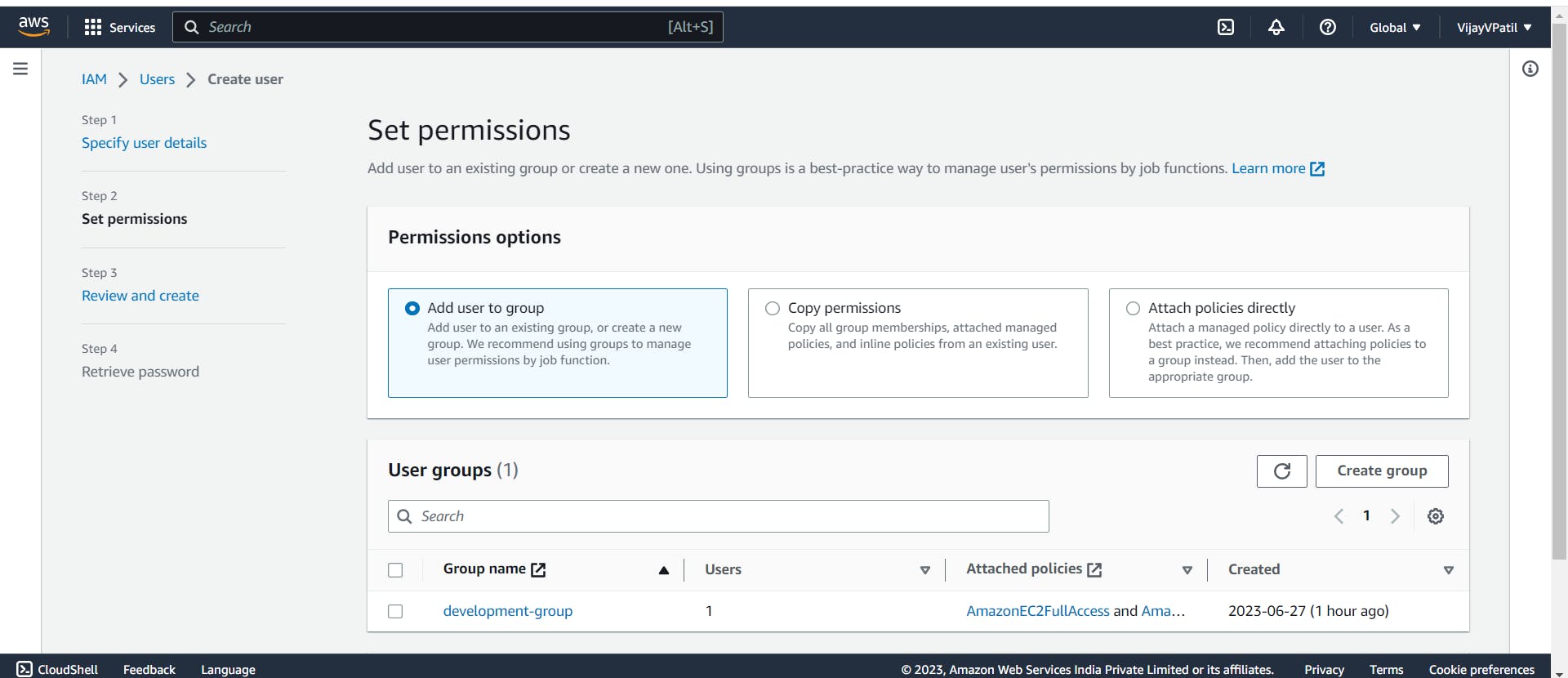
Now select the "Add user to group" and click on Next
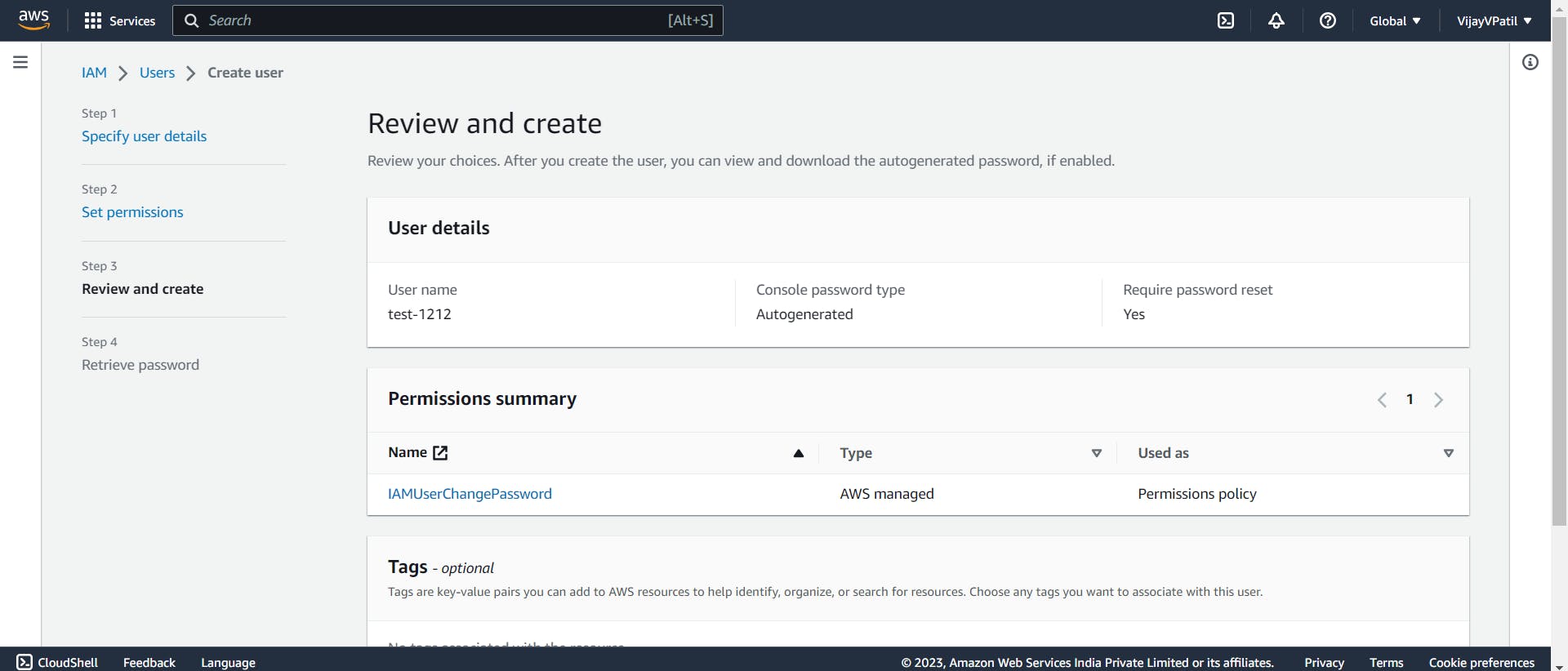
Click on Create User. After this we get a option to download a csv file . This CSV file contains user ID , Temporary password and and console sign in url. In this URL you have we have a number called "Account ID (12 digits) or account alias". When the first time we log in we need to change the password.
How to enable Policies
After logging in we navigate to any service. For ex: we navigate to S3 and we will be able to see we are denied the services. For this we need to enable policies to IAM user. Enabling policies means we need to give permissions to IAM users. For this login as Root Users.
Navigate to IAM-> Users and click on user
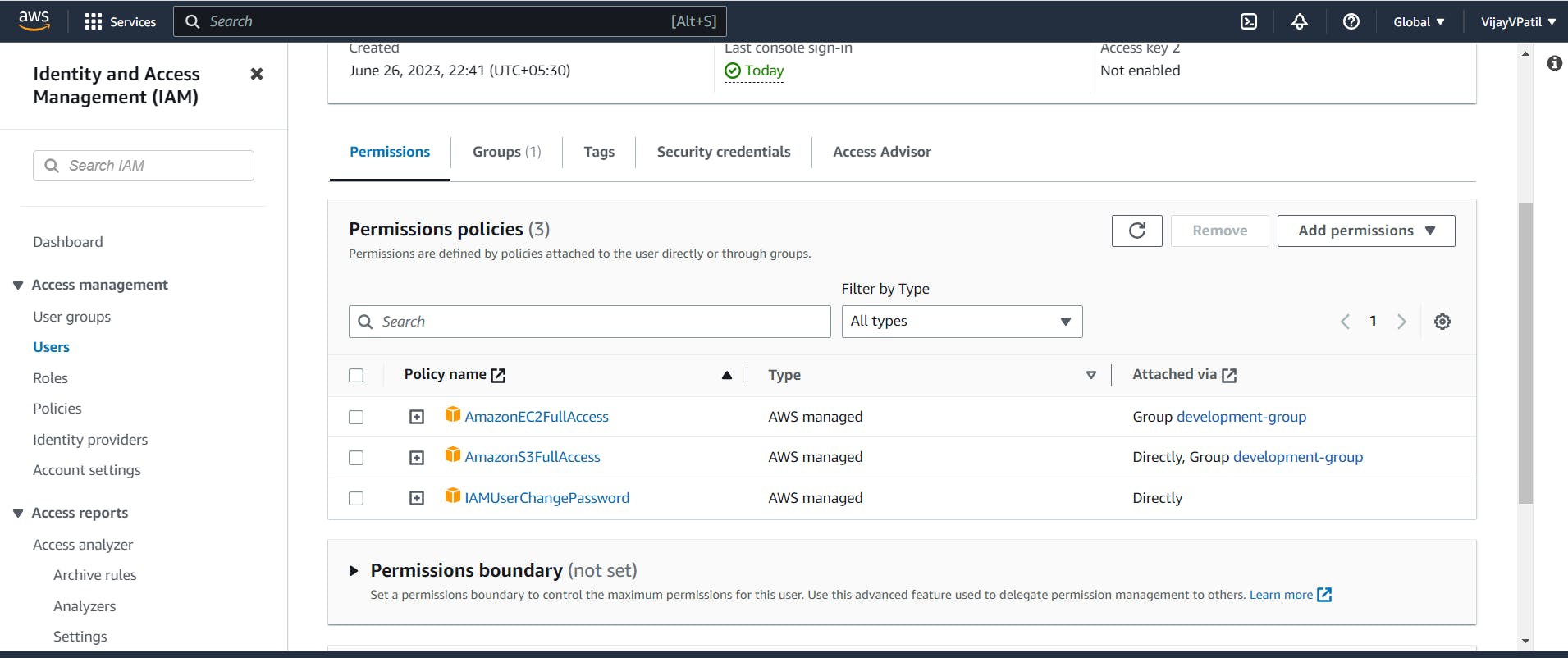
And click on Add permissions -> Attach policies directly. Search for "s3 full access" and click on '+' .We will be able to see policies written on JSON format. Tick on the policy name and click on Next and Add permission.Then the S3 Full access permission is added.
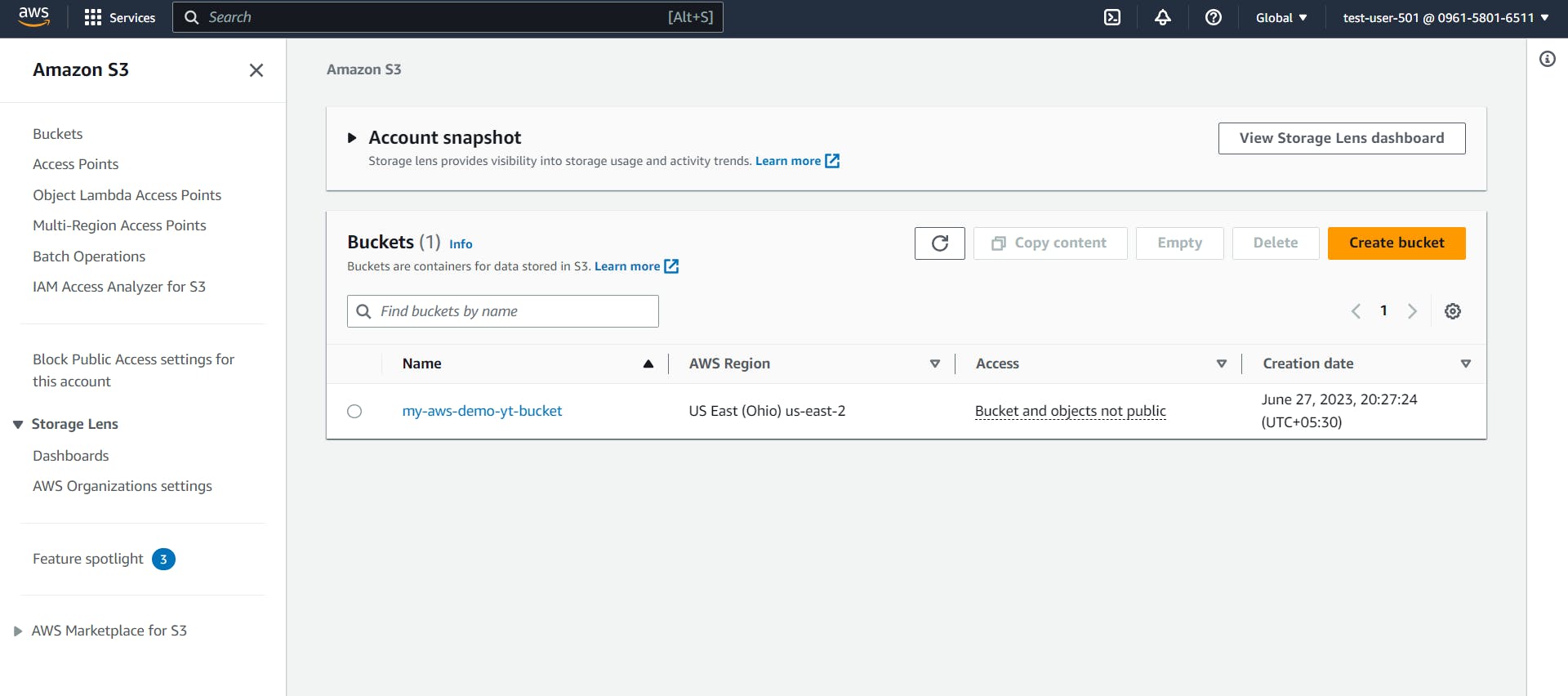
Now login as IAM Users. Navigate to S3 and we will be able to see S3 buckets if the AWS account has any. Here in my example I have created the s3 bucktes already.
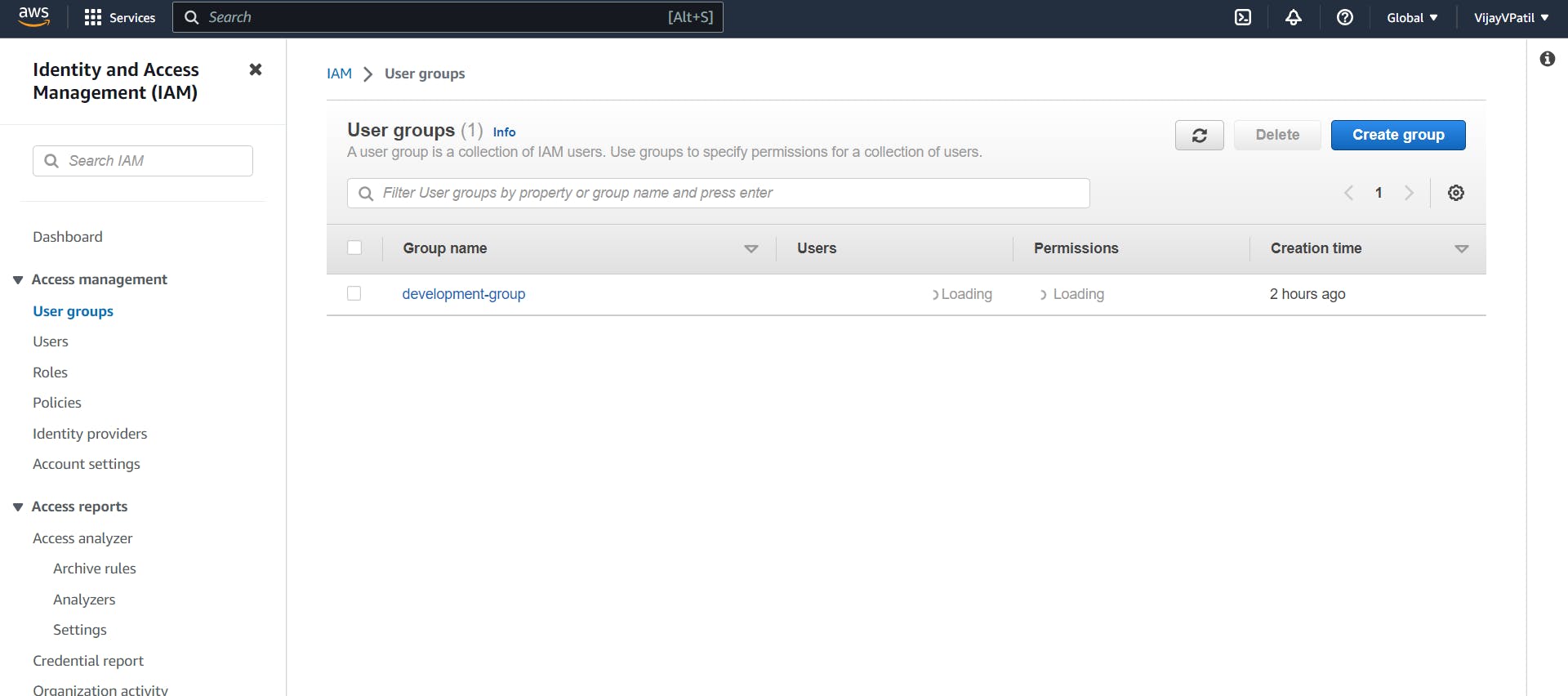
How to Create Groups
Navigate to IAM-> User Groups -> Create Group
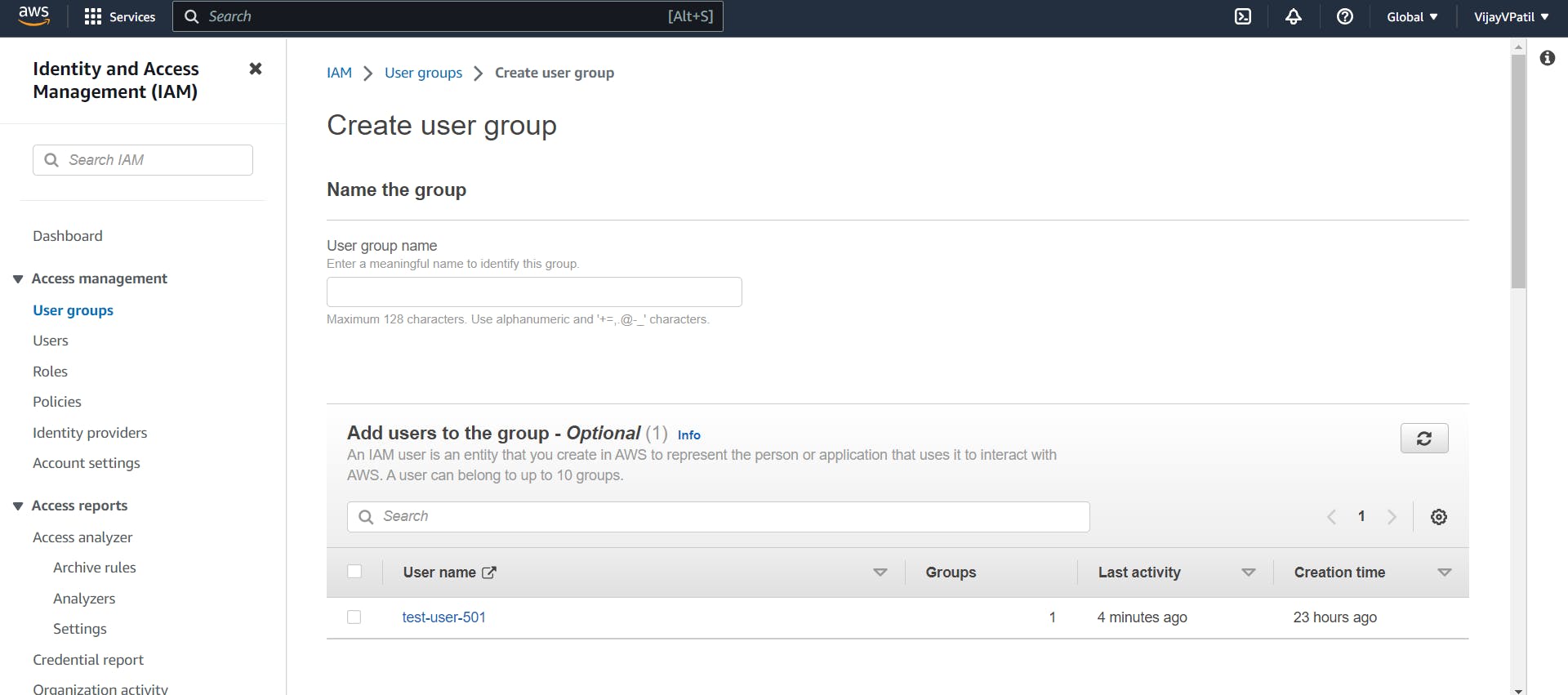
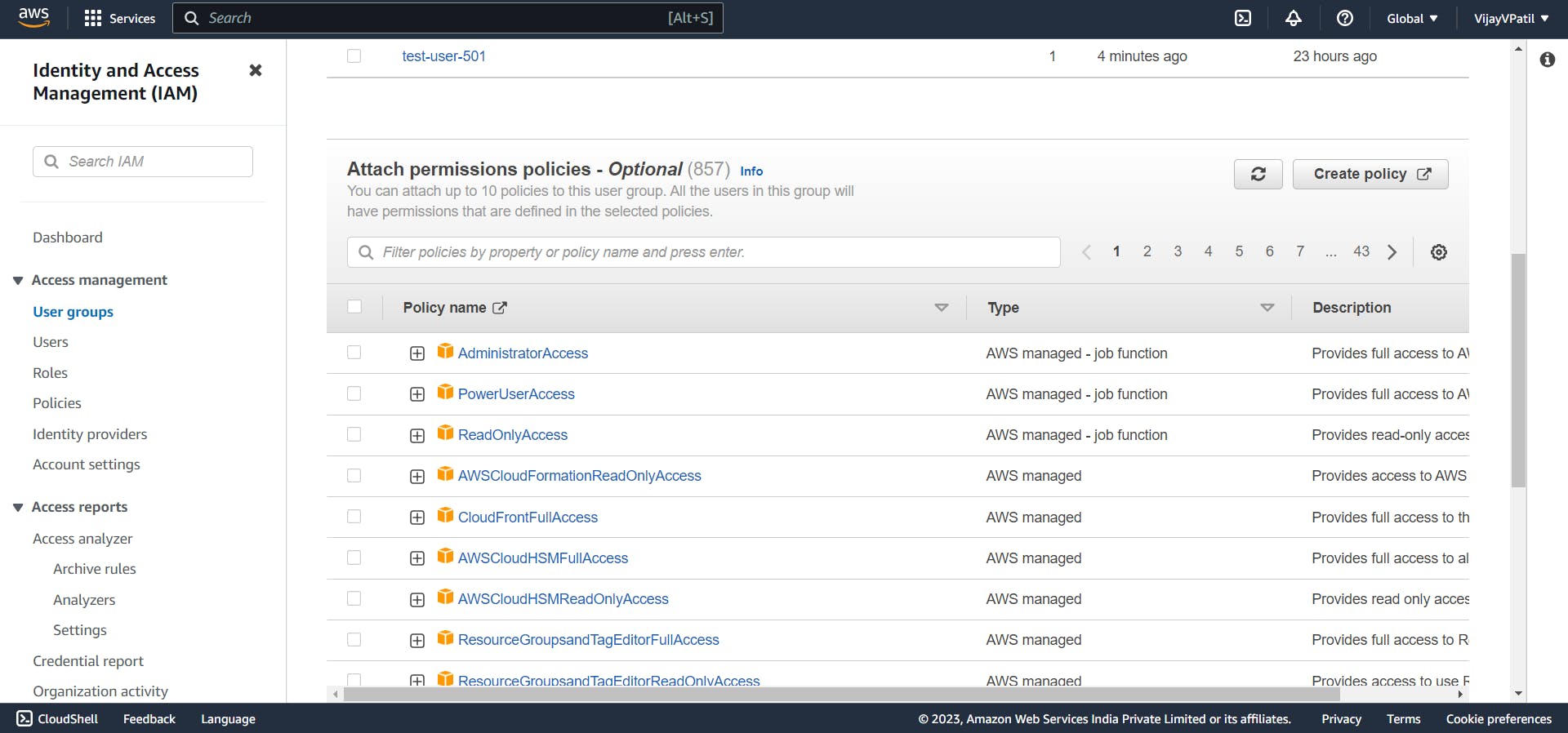
Enter Group name. Add the IAM users to the group. We can add multiple users to the group. To attach permissions to the group tich on any box besides the permissions and click on create group. This is how we create the group. Now the IAM users added to the groups will be able to access the services using the policies attached with the groups.
Resources:
AWS Zero to Hero by Abhishek Verramala: https://www.youtube.com/watch?v=mCLYcsJ0GXQ
AWS Documentation : https://aws.amazon.com/
